Cybercriminals are targeting the Indian e-commerce industry with an unprecedented strike rate today. Indian e-commerce companies, SMEs in particular, are the most vulnerable to cyberattacks owing to their lack of preparedness in identifying and managing new types of digital risks.
As big data explodes and funding for e-commerce companies increases, they become easy targets for cybercriminals. In response to these threats, e-commerce businesses readily pounce on every opportunity to fortify their IT efforts using sophisticated digital tools and analytical solutions. The IT systems become more complex with limited visibility and poor authority, and as a result, these businesses enter a never-ending race against invisible cybersecurity risks.
In 2023, Indian organizations bore the brunt of ransomware and crypto-jacking attacks. These attacks were laser-focused on targeting the critical IT infrastructure that supports cross-border payments, IoT-based applications, and data management systems. Despite an increase in IT spending on cloud security and data center transformation, there are no signs of an improvement in cyber risk management for e-commerce companies.
E-commerce SMEs can mitigate cybersecurity risks by adopting a proactive approach to an intelligent digital transformation using world-class data integrity and infrastructure security solutions.
But first, let’s identify the top cyber risks inflicted on e-commerce SMEs.
In this article, the biggest cybersecurity risks and challenges for e-commerce SMEs and what business owners should do to address these security threats have been identified.
#Risk 1: Social Engineering Masquerade Big Brands
Social engineering was the most prevalent cyber threat in 2022, beating financial data theft.
Shopping on e-commerce sites can be a rewarding experience. But what happens when cybercriminals impersonate your e-commerce brand and fox your customers into e-skimming?
Big discounts on sales festivals, integrated payment options, Buy Now and Pay Later facilities, fast-paced delivery services, and countless other customer-focused experiences make e-commerce shoppers queue up for prime-time sales days. This is an ideal opportunity for social engineering scammers.
Scammers play the “make-believe” game by manipulating and influencing shoppers into clicking links or asking them to fill out forms asking for personal information (name, phone number, DOB, email, location, and others).
Employees could also fall prey to social engineering tactics.
Baiting, phishing, spear phishing, CEO fraud, and pretexting are some commonly used social engineering techniques applied to e-commerce websites.
All it takes is one social engineering SQL injection or DDoS attack to take down your entire IT infrastructure.
Solution:
E-commerce companies should adopt a reliable Identity and Access Management (IAM) system for superior password management using RBAC and log-in or activity monitoring. This protects users and employees from falling into the social engineering trap.
Another potent means to fight against social engineering cyber risk is to modernize your application vulnerability assessment and testing. Vulnerability testing on PaaS platforms using data integrity solutions can prevent cyber criminals from inflicting social engineering attacks on your e-commerce properties.
#Risk 2: Ransomware Crimes Gather Momentum (and, Dark Web Marketplace)
Less than 0.03% of the internet data ever produced is visible on the surface; the rest is all part of the dark web or deep web marketplace. Ransomware data ends up in the dark web marketplace.
Is your organization’s data safe?
2023 witnessed a slew of ransomware attacks on e-commerce sites globally. The number of ransomware attacks and the severity of these risks show the advancing nature of technologies and tactics in the IT industry. For example, ransomware attackers use artificial intelligence-driven techniques to launch automated attacks on e-commerce websites.
Access to high-speed internet, the democratization of cryptocurrencies, and deteriorating data management practices are all responsible for this massive influx of ransomware-led attacks on e-commerce SMEs.
A majority of ransomware victims do not realize their systems have been compromised until it’s too late for them to recover data and take control of their IT resources. That’s where ransomware agents mint money. Moreover, many enterprise victims have reported suffering a second ransomware attack within a year of the first attack, mostly from the same criminal group.
Solution:
E-commerce SMEs could adopt a “prevention is better than cure” approach to overcome ransomware attacks. SMEs should have a regular audit of the IT infrastructure, including quarantine of remote workplace assets, as part of the overall IT modernization operation to strengthen data integrity and data recovery.
#Risk 3: Shadow IT + SaaS Sprawl: How Mismanagement Impacts Cybersecurity
SaaS sprawl has snowballed into a major security risk in 2023. Cybercriminals are exploiting IT sprawl with ease.
SaaS mismanagement in e-commerce emerged in the COVID era when employees moved to a remote setting. Like most industries, e-commerce continues to suffer from the growing menace of shadow IT along with SaaS sprawl.
Many staff members install unverified and unauthorized hardware and software applications without the approval of the IT team. This exposes the IT infrastructure to external risks, in addition to causing another problem called SaaS sprawl.
Employees and associates may use numerous cloud-based software patches and applications for tasks such as file sharing, communication, collaboration, data storage, and automation. These “unseen” assets are susceptible to external threat groups, potentially resulting in an uncontrollable security crisis.
Solution:
SaaS audits and procurement management can neutralize the security risks of shadow IT practices. An IT auditing service provider creates an IT modernization roadmap aligned with your financial figures and graphs. E-commerce SMEs can benefit from auditing services to measure and manage enterprise IT requirements in an integrated, risk-proof environment.
#Risk 4: Overlooking BCDR Functionalities
A cyberattack is an existential threat to every organization. However, most organizations hit by a cyberattack are able to recover quickly if they have a business continuity and disaster recovery plan in place.
E-commerce, by virtue of the nature of their business, the size of their IT budgets, and the customers they service, is most vulnerable to digital risks. But do e-commerce companies fare well when it comes to business continuity and disaster recovery?
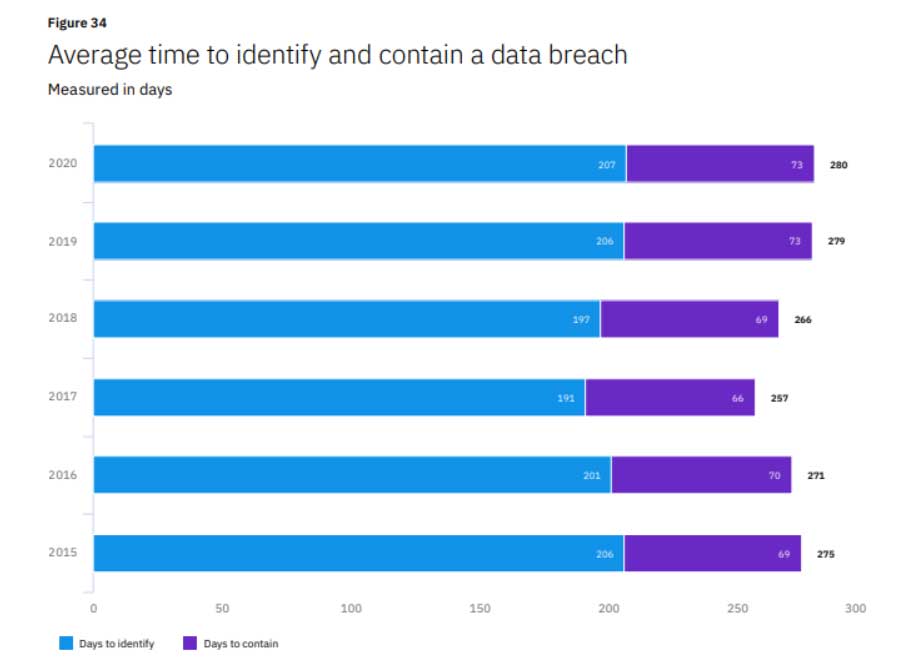
According to a report, it may take a company over 200 days to identify a breach and even more time to recover from it. The combined average time span, referred to as the data breach life cycle, is 279 days.
Making an intelligent guess: Indian e-commerce SMEs, which have fewer IT and security experts in their teams, could have a longer data breach management lifecycle.
India-based E-commerce SMEs face mammoth challenges in integrating their IT modernization efforts with cyber security resilience. Most e-commerce IT teams fail to embed business continuity and disaster recovery (BCDR) processes and policies as part of their IT resilience. Without BCDR, IT teams lack the ability to break down departmental siloes and replace outdated resources and technologies with a more compliance-oriented infrastructure. This leads to problems associated with SaaS sprawl and shadow IT.
Solution:
Automation is a key enabler in the overall BCDR program for e-commerce companies. It could include state-of-the-art IT security management solutions such as intelligent surveillance. BCDR processes include the smart integration of various AI and automation capabilities.
These capabilities include advanced technologies such as facial recognition, OCR, threat predictive intelligence, intelligent image processing, analytics, and remote asset management. BCDR programs for e-commerce could also allow for integration with enterprise firewalls and other digital asset management and IT security measures.
#Risk 5: Human Errors: Tackling IT Inefficiencies
Human errors accounted for 40% of reported outages in recent years. These errors often stem from a failure to comply with existing data management norms and regulations, a lack of automation tools, and IT inefficiencies. Indian e-commerce SMEs are also at risk of falling victim to cybercriminals due to human errors. For instance, employees may set weak passwords that can be easily cracked using brute force tactics.
Similarly, employee negligence associated with sharing passwords with others or failing to comply with BYOD or public Wi-Fi network connections can lead to human error-linked cyberattacks.
We can also count deliberate sabotage by internal human staff as part of this list. Disgruntled employees could leak sensitive data or co-participate in ransomware attacks to extract financial gains in exchange for information from their current or former employers.
Solution:
It is impossible to think of succeeding with modern IT practices without Zero Trust Architecture (ZTA) and behavioural analytics. IT modernization best practices should adopt new-gen technologies for ZTNA, behavioural analytics, predictive risk assessment, and elastic log monitoring.
How to Respond to Cybersecurity Needs: Best Practices with Examples
According to a Gartner report, nearly two-thirds (72%) of organizations have limited disaster recovery capabilities. Most suffer from the illusion of being fully protected against cyber risks by their existing IT infrastructure.
It can be a daunting challenge to justify all the IT modernization goals and investments if the organization fails to safeguard its digital resources. That’s why you need new solutions to tackle new risks.
Adopt AI and Machine Learning in IT Modernization Lifecycle
E-commerce IT leaders should find new ways to stay ahead of cyber attackers. New-age artificial intelligence and deep learning techniques could be used for anomaly detection. These AI systems help the IT teams create security baseline models, identify data deviations from the baselines, and set up data observability tools to track health and prevent security incidents.
Embed Security Knowledge Management across Organization
E-commerce organizations should build a knowledge-based security management infrastructure. This adds heightened efficiency and security to multi-cloud environments. In an IT modernization roadmap, a reliable business intelligence tool such as Embee’s VirtuaPlace makes the workflow for e-commerce operations smooth and secure in challenging work environments.
Embrace Data Minimization
Storage limitations and cyber risks have led to the arrival of a new concept in the cloud called data minimization.
E-commerce SMEs could benefit from data minimization as part of Cloud migration and modernization practices. This would reduce the need to collect, analyze, and store unnecessary data. Less data in the repositories means fewer risks and lesser costs of operations required to manage this data.
Choose a reliable partner
Cyber teams can benefit by partnering with a reliable XaaS vendor that offers a broad range of services such as cloud migration, data integration, comprehensive security assessment, cloud modernization, and employee training and upskilling.
XaaS vendors such as Embee can strengthen e-commerce SMEs against advanced cyber risks with fully managed IT security and surveillance services. Working with an XaaS partner also enables SMEs to diversify their products and services at the post-M&A stage when they are required to limit the exposure of threats to data and performance.